Introduction to computer networking sections:
- Introduction to computer networking
- IP Addressing
- Servers and data centers
- Cloud computing
- Virtual private cloud (VPC), virtual machine (VM), and subnets
- Network latency and server latency
- TLS, public key, private key, and CA certificates
You should NOT read this blog post if you know everything about computer networking. The rest of you most probably know the feeling of attending a work meeting where you have zero clue what others are saying. Yes, that’s the type of meeting where you struggle to stay awake even though it’s your seventh coffee.
You could be completely new to the IT industry or already with some (senior) experience, but the problem is always the same – you are missing some of the computer networking fundamentals. But, of course, you are not confessing this to yourself since you always have X other (more important) things to do. And yes, others think that you know (especially if you are, say, an architect).
NOW it’s the moment where all the acronyms that always confused you will be disentangled. It’s the moment when you are going to feel an immense power of confidence and the burden being lifted from your shoulders. From this point on, no one is going to doubt your knowledge anymore! And it doesn’t matter if you are a senior, junior, or just switching to IT – the text is written so that everyone can understand.
My journey with networks
I found myself in a similar situation since I completed finance-related studies but ultimately decided to switch to software engineering. The reason for this was a much better salary and career path. For example, in Europe, you can earn even 75k-95k EUR on the payroll after 2-3 years.
I moved quickly through the career ladder and found myself in a senior IT position. Soon, I discovered that I do not truly understand some of the computer science fundamentals. (Share your career path in the comments).
After a few years of computer science books and a few 2-3 months courses (there is a shorter path also), I can say that I am now on a good path. With this post, I am going to share some of the most important concepts in computer networks that you must understand for a successful career in the IT industry.
What’s here for you
This article is great to cover the gaps (if you are already a senior) or to start confidently if you are at the beginning of an IT career path (or changing to IT).
The knowledge of computer network fundamentals can help you climb to the (more) senior position levels rather fast since most IT professionals actually miss this part (more or less). So, you will have the knowledge others do not have if you make it to the end.
Also, IT job interviews always require some knowledge of computer networks. It doesn’t matter if you are applying for a programming position or operations related, the networks are always there! By the end of the post, these questions will be a piece of cake for you!
Before we dig into the introduction to computer networking 101, it is important to understand that in IT it is all right not to know something as long as you want to learn it. (If you are interested in knowing more about Python read this post).
If you look at any of the job postings, you will often see lists of unrealistic requirements that actually demand an entire department rather than an individual. Compliments to all of you for the courage you show by being in this field!
Now, let’s warm up with the definition of a network (not a computer network still!) provided by Oxford Languages.
A network is a group or system of interconnected people or things.
… and now let’s get this to the level of computer networks which brings us to the first concept.
1. Introduction to computer networking
Similar to the general definition of a network, computer networks are nothing more than a bunch of computers connected with each other (see, that was easy).
The word to watch for is “connected”, so what is connecting these computers? The answer is cables!
There are several different technical components that are involved here, but at this point, it is important to understand that there is no MAGIC, it’s all cables!
The internet network
So if you are “connected to the internet” (the internet being a bunch of interconnected computers), you can physically track cable from your modem to another’s computer modem that might be on another end of the world — (if you don’t have anything smarter to do).
Here is a picture of these cables at the ocean bottom.

…and there is a picture of all the underwater cables that exist across the continents.
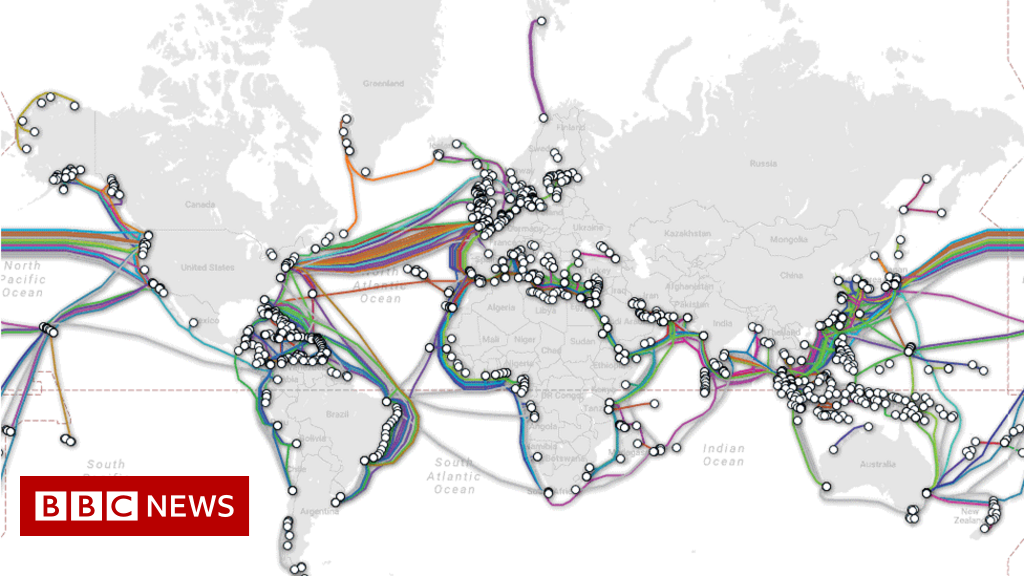
These cables, therefore, serve the purpose of transmitting electrical signals issued by one computer to another/other computer(s) in the network. The electrical signals hold the binary code that reflects, say a chat message (PDFs, music, photos, … also). In more technical terms, the content travels via MESSAGEs that get broken up and organized into smaller units called PACKETS (I wrote another post to explain these in detail).
Once the binary code reaches the end computer (via the network), that computer’s hardware understands the binary code and translates it for you to the human-readable format (that’s how you can watch funny cat videos on YouTube when you are bored).
Local networks
As opposed to WWW (world wide web, a.k.a. the internet) there are also much smaller computer networks that you are using every day (non-public networks).
These are devices that connect to your computer via cable (and router) for instance. If you ever played Counter Strike 1.6 with your friends in a LAN (local area network ), you have a very good idea of what these smaller-scale networks look like (also if you ever printed something).

Now when we know — cables, cables, and cables! — we can understand the networking fundamentals on a high level.
Here is the full path of travel via the internet network: you take a photo of your cat (with the desire to send it to a friend on another continent) and click that send button. The binary representation of that photo reaches your modem via cable or WIFI (WiFi uses radio signals). Then this signal travels over the cables from the walls that are installed by your internet provider (e.g., T-Mobile, Ziggo) and further through the cables installed in the ground of your city (if you don’t know what are local internet providers just wait for the first YouTube ads since they are bombarding with these!! ).
By traveling, this signal is moving through the cables OWNED by different companies (internet providers) or government-related authorities of different sizes since most of those under-sea projects are huge infrastructural investments done by conglomerates and different countries.

Once the signal has traveled the undergrounds, the seas, and the oceans it has finally arrived at the destination country and now has been taken by the local internet provider cables and ultimately reaches the walls of the receiver (your friend) and her modem and computer.
And here is that cat photo I am sending you via the same logic!

Now that we understand the high-level infrastructure, we can go a level deeper and better understand the second important concept which is IP addressing.
P.S. Write a comment if you need any part of the introduction to the computer networking section clarified or if I said something odd here.
2. IP Addressing
Your home address is a combination of your name, surname, city, street + number, zip code, and country. You need all of this so that the postman can deliver all the strange things you are buying on AliExpress EXACTLY to you and not to your neighbors.
Since computers are also communicating with each other over the internet (cables), there must be a way to uniquely identify each of these. In the computer world, an IP address serves the same purpose to computers as your shipping details — to identify an individual (computer) in the sea of computers.
Public IP address
Every computer that takes part in the global computer network (the internet), has a public IP (address) assigned to it (by your internet provider company, which is also called – ISP – internet service provider). [Read here about how ISP helps resolve the domain name into an IP address].
In more technical terms, a device can have IPv4 and IPv6 IP addresses assigned to it. The IPv4 example would be 143.176.147.29 while the IPv6 example looks like 2001:0db8:85a3:0000:0000:8a2e:0370:7334.
Since the public IP address must be unique for each of the participating devices, you can already figure out that IPv4 has a finite number of addresses and therefore a finite number of devices to be assigned to. So the world is running out of these very fast.
Due to the growth of computers participating in the network, the smart guys have come up with IPv6 which we are not going to exhaust any time soon. For simplicity reasons, I am going to refer to IPv4 when writing ”IP address” in this text.
Now, public IP addresses are called public because these are known to all the participants on the internet. That is how your public IP address can be used by others to locate you and send you virtual content. In other words, two computers connected to the internet need to know their respective public IP addresses to talk to each other and exchange messages across distant locations.
If you haven’t left this post so far due to all the abbreviations in the last paragraphs, a fair question to ask at this point is: if there is a public IP, must there also be a non-public — private IP?? Yes, you are right — there is something we call a private IP address as well.
Private IP address
Below are classes of private IP addresses together with ranges.
A: 10.0.0.0 — 10.255.255.255
B: 172.16.0.0 — 172.31.255.255
C: 192.168.0.0 — 192.168.255.255
These are excluded from the public internet, and no device can have a public IP that belongs to the above ranges — these are reserved for private networks by an internet authority called IANA (Internet Assigned Numbers Authority).
Earlier, we mentioned that a computer network could also be a LAN (local) network that does not have a gateway to the internet. In such an environment, the devices also use an IP to communicate with each other — the PRIVATE IPs this time.
For instance, your laptop might be recognized by the private IP of 192.168.1.5, your printer 192.168.1.6, or your smart TV 192.168.1.7. All these IP addresses are only valid within your local network.

The biggest advantage of private addresses is that they can repeat across different local networks.
This means that your friend can have a local network with his devices having the same private IP addresses as the ones from your local network. Thus, no need for UNIQUE private IP addresses since we can reuse them.
Quiz time
Before we move on to the next concept, let’s see if you get this joke.
…and? All right, let me explain. Your computer has internal processes that use the private IP of your computer to call themselves. Most computers recognize this address as localhost — it can also be in the IP format such as 127.0.0.1. Since localhost is the home to those processes, the joke is a geeky way of saying, “there is no such a place as home”.
… that’s it, you made it through the second concept (and its abbreviations) without slamming your mouse against the wall. Keep moving on and share any questions you may have in the comments section.
Now, let’s jump to the third concept, which is… (drums sound) — servers and data centers!
3. Servers And Data Centers
Understanding networking fundamentals always assumes an understanding of what a computer is – NO, I am not kidding! Most people think of computers in a way similar to this photo.

If you are that old to recognize this “Windows 98” message, I am sorry for that. But back to the computers. This one contains a monitor, mouse, keyboard, and COMPUTER CASE. You need all these components to interact with the user interface (programs) that appears on your monitor.
What do you think that the most important component of the listed ones is? YES, it is the computer case. If you were curious enough as a kid, you probably opened some of the cases (and did not know how to put them back afterward).

If you did, you have most probably seen that the computer case contains all the crucial components for the computer to operate, the rest is only aesthetics (monitor, mouse, etc.). These core components are the motherboard, graphic card, RAM, disc, cables, network card, processor, etc.
Servers
Now, if this computer can be commanded remotely, you are on the right path in thinking that the computer could be reduced to the computer case only. And if any of my writings here is worth anything, you already understand that computer networks allow computers to command each other over cables. This brings us to the concept of a “server,” which is nothing more than a computer reduced to its minimum components, connected with other computers via LAN or the internet (or both).


In reality, most computers connected over the public computer network (the internet) are called servers and look exactly like the ones above (well, maybe not 100% exact, but you got the point).
Why should you care about these servers at all? Because all of the internet content that you are accessing every day (Spotify music, Instagram photos, YouTube videos, your bank’s app) actually lives in a server box. Even when you type google.com in your browser, you are calling the server thousands of kilometers away to collect some of the content out of its disc.

Data centers
The servers usually operate on Linux OS (sorry to the Windows fans) and are stored in big warehouses that are called data centers. Data centers are, therefore, buildings that store servers that store data.

These data centers have some time very cool features. During my time in one of the financial companies, they had their own data center with a floating floor (where the server racks are) so that in case of a flood, the floor rises with the water and servers stay dry.

Another data center I have been to, owned by Google, has diesel engines as a backup in case of electricity outages.
In practice, most of the data centers are owned by big companies such as Google, Amazon, Microsoft, and other companies involved in providing hosting and infrastructure solutions (also government organizations).
With all these big names also comes security since these servers hold the data of billions of people. It is understandable in this situation that all the high-tech features, such as floating floors and backup (diesel) power serve an immense purpose since the servers must stay online constantly – to earn money!
What happens if the servers are offline? Then Facebook cannot earn money by showing you their dropshipping ads since the website is not accessible and no one sees them!
Expectedly, I only scratched the surface regarding data centers and their infrastructure – there is much more. For now, you must get a high-level understanding of how the system works, and in another post, I can bore you to DEATH with all the nitty-gritty.
… FINALLY, you reached the end of our third important concept of networking fundamentals. Go and get some coffee now (and come back).

4. Cloud Computing
If you are breathing air on this planet, you must have heard the buzz-words such as AI, MACHINE LEARNING, CLOUD… (please report if you did not!) And it does not matter if you are already in the industry or just starting since these words are HUGELY OVERUSED (because people sound smart while saying them). Now, you can tell by the sound that I am not the biggest buzzword fan – so let’s clear some doubts immediately.

And to put it in text format, “there is no cloud, it’s just someone else’s computer” – if you understand this meme, you understand cloud computing. To have a complete view, let’s explain how cloud-thingy has evolved to these popularity scales.
Pre-cloud era
If you needed a server around 15 years ago, you would typically call a server company (also called a hosting provider), wish them a good morning (if you are polite), and order 2x dedicated servers for your business needs (let’s say you wanted to create a store for your cat-clothes business).
You would “rent” these servers (also called physical machines) and pay for them every month in the same way as you are renting a car and paying per day. Regardless of the usage, you are paying for both the car and server for the period you rented them.
So the value for the money here was the “bare-metal” machine that is running in someone else’s data center that has a public IP (and an operating system) you can connect to (including networking, provisioning, physical security, etc.). That was basically it; you are further responsible for maintaining your servers, including the OS updates, security patches, and similar.
Some traditional institutions (banks, governments) still work this way and have their own data centers that store the data on bare-metal machines.

Now, what happens with your cat clothes store when Black Friday hits? Yes, the servers you rented are not enough to serve those huge traffic spikes, and you have to go back to your hosting provider and rent another server for at least one month (even though you only need it for a few days).

The hosting provider might have 1000 similar shops. Perhaps all the owners need the servers on short notice, and only temporarily, so the company must plan for this and procure the necessary hardware on time.
…but what happens when the peak traffic has passed, and the store owners just do not want to rent those additional servers anymore? They return it, and now the hosting company has 1000 spare servers and huge inefficiencies in their business because the servers earn money only when they work!
Cloud era
Because of these inefficiencies and room for profits, the bigger players entered the hosting market and commercialized the entire industry. Amazon, Google, and Microsoft have given birth to their CLOUD offerings which are AWS, GCP, and Azure, respectively (this means AWS is Amazon’s and so forth).
Since these companies already had know-how in data center building and management (for their purposes), they started offering data center services to the public. And all that on-demand, only when you need it, as long as needed, and all in one click (sounds like a terrible sales phrase).
Here is a short video of the inside of an AWS data center. (Read my other post on getting started with AWS here).
All the public cloud providers are now offering many different services, and I am not going to list all of these — because I cannot remember them all and because you would have left this post since the list can be extensive. Let’s try to understand the benefits of one such service.

Cloud computing benefits
If we take, for example, a virtual server that you rent from AWS, here are some benefits that your cat-clothes store can have.
- The server is ready in 3 minutes, and you are paying per second (minimum of 60 seconds)
- You can provision and destroy as many servers as you want with no obligation to inform anyone in advance
- Computing resources are cheaper than in the pre-cloud era
- Selection of a region where you are going to store the data — AWS has data centers that are globally present
- More secure data center
It is relatively easy to see that cloud providers offer a lot of benefits compared to traditional hosting providers. The benefits are great for companies that used to have huge costs in maintaining their own data centers and hiring skilled engineers.
Now that you know what “cloud” is, you can put your online cat-clothes store directly on the cloud and enjoy some respect in your friends’ circle because of your cloud storage.
But remember, there is no cloud; it is just someone else’s computer (Amazon’s, Google’s, or Microsoft’s).
…after a short commercial break, we are going to the fifth important concept of our introduction to computer networking: VMs, VPCs, and Subnets.
P.S. Write a comment if you like cats.
5. Virtual Machine (VM), Virtual Private Cloud (VPC), and Subnets
More abbreviations??? You are doing fine so far, so let’s dive in!

Virtual machine (VM)
A virtual machine is just that – a virtual (not real) computer called a virtual server. The base for these VMs is, of course, physical servers that exist in the physical sense in a data center.
The trick is that the VMs and the underlying physical servers are not in a 1:1 relationship. This means that one physical server can accommodate multiple tenant VMs. These VMs SHARE the underlying hardware (CPU, RAM, disc) of the same host server (physical server).
It is similar to your university years when you lived with flatmates, and everyone shared common rooms (living room, bathroom, kitchen). So in this sense, multiple tenants share one apartment’s rooms – in the same way as multiple VMs share the same physical server.

As you can see, VMs are very well optimized to do two things 1) use the most out of the physical hardware and, by doing that 2) squeeze all the possible profits (since one machine can be rented to multiple customers).
Therefore, VMs are one of the basic offerings of all the major cloud providers — it’s just that Amazon, Google, and Microsoft use different names for the same thing. AWS calls VM — EC2 (Elastic Cloud Compute instance), GCP — Compute Instance, and Azure — Virtual Machines.
Without going too much into technical details, VMs actually run on top of the host’s operating system that uses a hypervisor process to provision these VMs. From that point on, VMs continue life independently by having individual operating systems that others can interact with.
All these VMs are said to be logically isolated from one another and unaware of each other’s existence. You can also see this as one physical server (host) accepting multiple guest VMs and letting them run independently.

Virtual Private Cloud (VPC)
Now, in the cloud setup, VMs live within a network. AWS calls this network a virtual private cloud (VPC), and GCP calls it Project.
Within the VPC network, all the VMs can talk to each other via the Private IPs but also connect to other services that live in the same VPC (storage services, for instance). So, VPC is a logically isolated network that contains resources that are aware of each other.
To understand better, this is conceptually similar to your LAN (home network), where your devices can talk to each other. Still, no other network devices can participate in the communication (without you allowing it).

If you are still reading this LONG post, you rock — I would not last this long (if I hadn’t written this thing myself).
…Back to the topic now.
I explained that VPC is where VMs live, but there is more to it.
Subnets (Subnetworks)
VMs and other resources reside within something called a subnet (subnetwork) within a VPC. So, network within a network.
There are projects spanning thousands of VMs, and for efficiency (and security) reasons, VMs are usually classified in subnets. A good analogy that can serve here is a tall business skyscraper where every floor is a subnet of computers that belong to the network of the skyscraper.
What is so special about subnets is that they determine the private IP ranges that VMs in that subnet can have. Also, all the VMs within the same subnet can connect via the private IP.
To understand the subnet creation, we have to look at the construction of an IP address. For instance, the below IP contains 32 bits — 8 bits for each of the four numbers (each number having 1-3 digits).
192.168.0.0
So, the places between the dots can have up to 8 bits each – giving a total of 32 bits (allowed numbers are from 0 to 255 – for instance, an IP of 192.168.255.0). I know, this is when you start yawning but bear with me; it will make sense.

Now, every IP address contains the NETWORK label and the HOST label within that network (that is, a physical device address). That said, an IP address can take one of the following forms.
network.vm.vm.vm
OR
network.network.vm.vm
OR
network.network.network.vm
If you do not understand this, a good comparison would be to think of your city and street address combination as a network label. At the same time, the house number could be an identifier local to your apartment building. For instance, number 28 would be my apartment number, but number 30 is already my neighbor’s apartment but STILL in the same building – the same street and city (the same network label)!
CIDR blocks
Subnets are usually created by providing CIDR blocks (Classless Inter-Domain Routing). Not to go into too much detail (I will do that in another post), the CIDR range shows bits allocated to the network part of an IP address, denoted by the forward slash /.

Let’s take, for instance, the following CIDR notation that we must provide when creating a subnet for our floor in the hypothetical skyscraper building.
10.0.0.0/8
So the network part gets 8 bits, and 24 bits go to the VMs.
This will result in 1 subnet with the individual device IPs ranging from 10.0.0.1 to 10.255.255.255.
If we allocate more bits to the network, we can have multiple subnets.
10.0.0.0/16
The above creates 256 subnets (1.0.x.x – 1.255.x.x) with 65,536 (256 x 256) possible VM IPs within EACH of those subnets (usually 2-3 IPs are reserved for other purposes) — more than enough for a 256-floor tall building.

By further allocating bits to the network part, you can split the network into even smaller subnets. Wisdom words: practice subnet splitting by using this calculator.
Subnet benefits
Before we finish the concept, the main takeaway is that you can use the subnets to spare the public IPv4 addresses. Public IP can be assigned per subnet, and all the hosts within that subnet can share the internet gateway (one public IP). (Note: some subnets do not need the internet gateway – private subnets).
Also, subnets are here to make the network administrator’s life easier – sort of a classifier – since it is easier to administrate and secure 10 subnets of 50 devices each than a pool of 500 devices. Think also of one giant subnet with million devices. If hackers penetrate that subnet, they have access to all the devices at once! So, subnetting also reduces the risk since you can implement different firewalls on a subnet level.

And finally, subnets usually involve computers that talk to each other frequently. What I mean by it is that all the computers within a subnet listen to the communication happening in the entire subnet. For efficiency reasons, it is, therefore, better to organize the network where this computer chatter is relevant to most network members (since they are all listening to it anyways).
All right, you see the light now! Still, I bet you have many questions – use the comments section – it’s just for it.
6. Network latency and server latency
Before I introduce some tech terms (and yes, you have already had enough of them), let’s try to understand latency using the watering hose analogy – say that you want to do something mean to your nephew – kids are fun to make jokes with.

So, you position yourself next to the water tap that has the watering hose attached. You wait for your nephew to take the other end of the hose and ask him to see what’s on the inside. It is all set – now you release the water tap and WAIT for a couple of seconds (depending on the hose’s length and diameter) for the water to reach your nephew’s face!
That’s it; we have done another stupid thing in our lives!
In computer terms, latency is a measure that counts time starting from the moment a request was made to the moment the resource is received (end-to-end or roundtrip latency).
Say you have a link; the moment you paste that link into the browser and hit the enter button, the latency counter starts. Once the page fully loads (you cannot see that loading bar spinning anymore), the counter stops.

What is happening in the background is that your computer is sending a request (via packets) over the public internet (a bunch of cables) to another computer far away that catches the request, processes it, prepares the response, and sends it back over the same network path to your computer.
To understand better, let’s consider two latency aspects: network latency and server (computer) latency.
Network latency
Network latency is the time it takes for an electromagnetic signal to travel the cables from your computer to that distant computer you are sending a request to (and back). It primarily depends on how physically far that computer is. The signal travels via optic-fiber cables which enable the speed of light travel (200,000km/s).

Even though it might sound extremely fast, the travel times depend greatly on the distance traveled.
Round-trip latency examples
Below are some examples of the round-trip network latency (1 second has 1000 milliseconds). You can understand these as FROM – TO (e.g., from Paris to New York and back).
Paris – New York —> 87 milliseconds
Singapore – Paris —> 165 milliseconds
Moscow – Paris —> 50 milliseconds
Paris – Amsterdam —> 5 milliseconds
This trip almost entirely depends on how long the cables are — like the hose analogy. So, when you MUST send a request, there is not much to do to improve these numbers — treat them as constants.
Server latency
The other side of the coin is the server latency. This is the speed at which the destination server processes your request and counts from the moment the request has arrived to it till the response is ready for sending back.
TOTAL LATENCY = network latency (round trip) + server latency
So, if the server takes too much time to respond (too many requests, a complex task that requires a lot of processing, and slow hardware), the total latency will be much higher.
Without going into too many low-level technical details, we now understand what latency is. I will explain how the signal travels (hops) through the public internet network and the involved devices in another post (I will spare you for now).
Congrats, you made it again!!
7. TLS, Public Key, Private Key, and Certificate
Do you use internet banking? If you are not stuck in the dinosaur age, I am sure that you have an internet banking app on your phone (my grandmother still signs the transfers manually, but she doesn’t read tech blogs). Now let’s use this to explain why the security of your connection matters.
Your payment request to your bank (say, to pay for an XYZ in an online store) is traveling over the public internet — XYZ being something you do not need but think you do — e.g., a pizza oven.

As you already know, the request is traveling (hopping) over a bunch of servers till the request reaches your bank’s computer. These servers have a public IP, and someone can steal (intercept) your credit card details along the way!
TLS (Transport Layer Security)
To reduce the likelihood of fraud, the smart guys invented TLS (Transport Layer Security). With TLS, when the connection is initiated from your computer, and the sensitive information is sent over the internet, no attacker can benefit from your private details since the data is scrambled (appears random) during the transit!
So, for everyone except you and your bank, the payment instructions will look like this.

The majority of today’s websites and apps actually use TLS. For instance, you can tell if a website uses the TLS protocol if it has the letter S in the URL (next to HTTP) — so, HTTPS. This goes together with a padlock next to the address (🔒).
Based on this, most modern browsers will not even let you access the websites that do not use the secured connection (TLS) — you might see the warning.
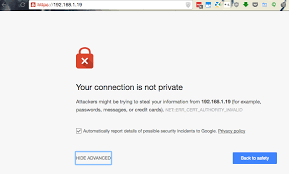
All right, you know why you should care for TLS. Let’s now zoom in and understand what’s behind the scenes.
TLS handshake
The secured connection between server and client is established via the TLS handshake process — client here means a device accessing the server. This can be a website (browser), mobile app (REST-API), CLI (command line interface) client, or anything capable of contacting the server.
Like this meme, the client and the server must acknowledge and authenticate each other (get to know one another) before they get into a closer relationship (a hug) and start transferring the data.
CA (certificate authority) is a middleman that facilitates this identity verification process.
Certificate authorities are companies that issue digital certificates that confirm the server’s identity. The certificate usually contains the details about the issuing authority, the certificate receiver (e.g., issued to ing.nl of the IP of 143.176.147.29), the expiry date of a certificate, and so forth.
Public and private keys
Once the certificate is installed on my bank’s servers, the server will contain something called public and private keys. The public key is a key that is used to encrypt (scramble) the data, while the private key is used to reverse the operation and decrypt the data (make it readable for humans again).
During the TLS handshake, the client understands that the server communicates via TLS, verifies its certificate against its certificate base (e.g., OS-wide certificates), and checks if it is still valid (not expired).
Once this is all good, the server sends its public key over the internet to the client, and the client then uses it to scramble the data it wants to send (your credit card details, for instance).
Once the information reaches the server, the private key decrypts the data (makes it readable again).
The trick here is that the data is encrypted with the public key that can be sent publicly but decrypted ONLY with the private key that is never sent over the public internet! Since the private key never leaves the server, the server is the only point to see the originally sent data (and you, the sender, of course).
That’s how the data in transit (traveling via the internet) is completely useless to anyone but you (the sender) and the receiver (the bank’s server).
TLS in a story
To make TLS even more intuitive. Imagine a wooden box that no one can open by brute force — but only with two keys. The box looks similar to this.

You get a task from a king to bring this wooden box to a distant empire, collect a secret message that reveals the hidden treasure, and transport the message back to the king in this safe wooden box.

The king gives you the public key (and his blessings), but he keeps the other (private) key to himself. He requests you lock the message in the box with the public key upon receiving the letter.
You cross the oceans and the mountains and finally get to that distant empire, collect the message, and lock it in the wooden box with the public key.

On the way back, many pirates try to steal the box and the key (and you lost it a few times), BUT it doesn’t matter — the public key can only lock the box!!
You bring the message in the wooden box to your king, and he unlocks the box by using his private key (the second key)!

At that point, the right person knows the secret, and since you helped, the king grants you ½ of the secret treasure!
To return to the computer world, the wooden box serves the same purpose as TLS, and the king mimics the server’s behavior. You, the messenger, carry the box through the wilderness (the internet), and the pirates (hackers) try to steal it.
With this seventh concept completed, you now have a high-level picture of how the internet network works. I am sure this knowledge can make a difference in your career since many IT professionals still do not own this subject completely (or not at all). There you have it; the knowledge of internet networks is only yours now (and the treasure)!
I will see you in the next post, hopefully not this long!
P.S. Since you are one of a few reaching the end of this post, I would like to know a little about you! Simply because I like hard-working, smart, and determined people! Write a short comment (or write me an email) about your current career and what plans you have!


![7 layers of networking explained to a plumber [True Beginner's Guide] 99E6B57F-559C-45EE-B3C7-775C198A6689](https://igorjovanovic.com/wp-content/uploads/2022/09/99E6B57F-559C-45EE-B3C7-775C198A6689.jpeg)
![DNS in computer networks for mortals [Explained] DNS in computer networks for mortals [Explained]](https://igorjovanovic.com/wp-content/uploads/2022/12/DNS-in-computer-networks-1024x536.png)

![Python Beginners Guide: The way rich kids are taught [2024] FA646E56-BD48-4528-9C03-E02D7E6142C3](https://igorjovanovic.com/wp-content/uploads/2022/09/FA646E56-BD48-4528-9C03-E02D7E6142C3.jpeg)

2 replies on “Secrets of computer networks demystified: 7 networking concepts to land any (IT) job40 min read”
Retiree learning a few things “in the cloud”
Keep up the good work!
i love the lesson since it has soo many computer words whose meaning i did not know ,yet i keep on hearing them from friends and websites as i research on coding and software development